Ensuring product authenticity with the help of a smartphones
Validate product authenticity by taking a picture

Secure & Authentic is a mobile application designed to empower consumers to instantly verify the authenticity of high-value physical products, such as luxury handbags, designer watches, and electronics. The app leverages advanced computer vision and machine learning to compare a specific, unique visual feature on the physical product—its "digital signature"—with a pre-computed digital signature printed on a certificate or on the product itself. This process provides a near-instantaneous and highly reliable authenticity check, combating counterfeiting and building consumer trust.
- Real-time Visual Feedback: The app provides a live overlay on the camera screen, guiding the user to the correct region of interest and indicating when the lighting and focus are optimal for a successful scan.
- Tamper-Proof Cryptography: By encrypting the digital signature, the signatures cannot be altered or or forged, ensuring the integrity of the authenticity record.
- Detailed Product History: Once a product is validated, the app can display its full history, including the date of manufacture, its entry into the supply chain, and any subsequent ownership changes (if the product is re-registered upon resale).
- Counterfeit Reporting: A built-in feature allows users to easily report a suspected fake product, providing valuable data to brands for tracking and combating counterfeit networks.
- Privacy-First Design: The app only processes the image of the designated "digital signature" region and does not require or store images of the user or the surrounding environment.
Want a closer look? In a personalized demo we'll show you how our product can meet your needs.
Every product is unique

Every natural surface has a unique texture that can be used to identify an object, similar to a human fingerprint. This concept is often referred to as "surface forensics" or "physical unclonable functions" (PUFs).
At a microscopic level, no two surfaces, even those from the same batch of material, are identical. The unique texture arises from the random and unpredictable processes that occur during manufacturing or in nature.
To use this unique texture for identification, you need a high-resolution method to capture it and an algorithm to process it. This can be done using a standard smartphone camera with macro lenses. The captured image is then analyzed by an algorithm. This algorithm isn't looking for a perfect pixel-for-pixel match. Instead, it extracts key statistical features of the surface's randomness. This includes the average roughness, the distribution of peaks and valleys, and the unique pattern of irregularities. These extracted features are then converted into a unique digital signature. This signature is the object's "fingerprint."
Download our comprehensive whitepaper to explore the future of product authentication and the business value it delivers.
How a Customer Authenticates a Product
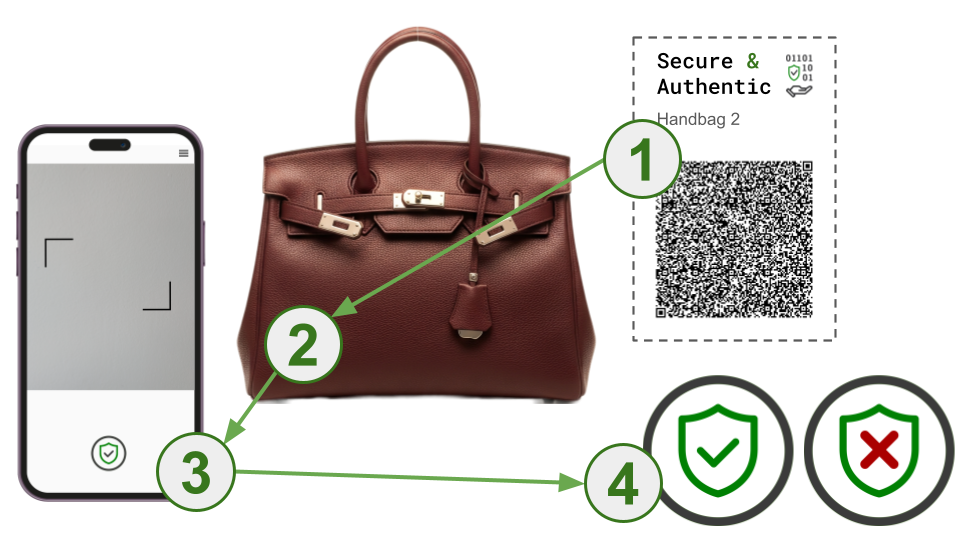
This process is a streamlined, user-friendly experience designed to provide instant verification of a product's authenticity. It bridges the gap between the physical object and its secure digital twin.
- Initiate the Scan: The customer opens the app and uses their phone's camera to scan a QR code located on the product's tag or packaging. This QR code contains the unique, immutable digital signature associated with that specific item.
- Capture the Physical Signature: The app's interface guides the user to take a picture of the product's designated physical signature—the area with the unique texture. This might be a specific stitch pattern on a handbag, a unique engraving on a watch, or the intricate grain on a leather wallet. The app's computer vision technology provides real-time feedback to ensure the image is correctly framed and well-lit for an optimal capture.
- Real-time Authentication: In the background, the app's algorithm goes to work. It extracts the physical unclonable function (PUF) from the newly captured image and converts it into a digital signature. This new signature is then compared to the original, cryptographically secured signature retrieved from the QR code.
- Confirm the Result: The system checks for a match within an acceptable tolerance. A successful match confirms the link between the unique physical product and its verified digital record, and the app instantly displays a clear "Authentic" status. If the signatures don't match, the app notifies the customer and provides options to report a potential counterfeit.
Interested? Contact us via email (info@lafirma.app) or phone (+49 711 - 21720705)
The Two Pillars of Forgery-Proofing

A cyber-physical signature's security is based on two core, integrated components:
- The Physical Unclonable Function (PUF)
Every natural or manufactured surface, from the grain of wood to the microscopic imperfections on a piece of metal, possesses a unique texture or pattern. This is its Physical Unclonable Function (PUF). Just as no two human fingerprints are identical, no two surfaces are identical at a microscopic level. The tiny, random irregularities that exist on a surface—such as the way a fabric is woven or the subtle pits and scratches on a metal component—cannot be reproduced with current technology, even with the same manufacturing process. This physical "fingerprint" is the anchor of the entire system. - The Immutable Digital Twin
The physical signature is then captured using a high-resolution camera or scanner. The data is processed by a computer-vision algorithm that extracts the unique features of the PUF and converts them into a unique digital signature. This digital signature is encrypted by the private key of the manufacturer. This makes the record immutable and tamper-proof. Any attempt to alter the digital signature would be immediately detected, as the modified data would not match the original cryptographic record.

